
leekie
-
Items
16 -
Registratiedatum
-
Laatst bezocht
Inhoudstype
Profielen
Forums
Store
Berichten die geplaatst zijn door leekie
-
-
Hallo,
Is me niet duidelijk hoe ik dit programma aan de praat krijg. Als ik het goed begrijp is dit geen kickstartprogramma, maar moet ik de exe starten op de geïnfecteerde computer door te dubbelklikken.
Dit terwijl ik geen inhoud van mijn computer kan bekijken of bereiken?
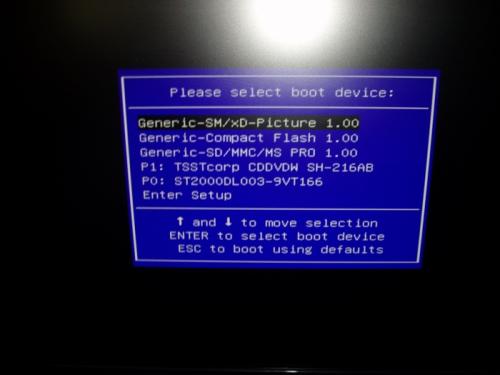
Herstarten en F8 geeft blauw scherm met BOOT info (zie 5 augustus)
Herstarten en F11 geeft Power Recovery scherm.
Wat doe ik fout, waar zit de kink in de kabel?
-
Nog altijd hetzelfde resultaat, jammer maar helaas!
De service User Profile Service verhinderd het aanmelden in Windows. Gebruikersprofiel kan niet worden geladen.
F11 geeft Cyber Link Power Recover" scherm.
-
Heb reboot gedaan na F11 toets (zie bericht 3 augustus). Nadien hitman pro x64 kickstarter geplaatst en opnieuw opgestart.
Heb met dit programma virussen verwijderd en een log afgehaald via USB stick (zie bijlage).
Bij de vraag om computer opnieuw op te starten blijft deze wel 'hangen ' op 'update 19 van 20'
Hopelijk hebben we hier voldoende info mee om verder aan de slag te kunnen.
Logfile:
HitmanPro 3.7.9.221 www.hitmanpro.com Computer name . . . . : WILLY-PC Windows . . . . . . . : 6.1.1.7601.X64/4 User name . . . . . . : NT AUTHORITY\SYSTEM UAC . . . . . . . . . : Disabled License . . . . . . . : Trial (22 days left) Scan date . . . . . . : 2014-08-11 20:58:51 Scan mode . . . . . . : Normal Scan duration . . . . : 17m 39s Disk access mode . . : Direct disk access (SRB) Cloud . . . . . . . . : Internet Reboot . . . . . . . : Yes Threats . . . . . . . : 134 Traces . . . . . . . : 135 Objects scanned . . . : 2.340.866 Files scanned . . . . : 116.746 Remnants scanned . . : 578.455 files / 1.645.665 keys Malware remnants ____________________________________________________________ HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Anti-Virus Professional.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntispywarXP2009.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntiVirus_Pro.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPro_2010.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirusxppro2009.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\av360.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brastk.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csc.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dop.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\frmwrk32.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gav.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbn976rl.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\homeav2010.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MalwareRemoval.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ozn695m5.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pav.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pc.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PC_Antispyware2010.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsAuxs.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsGui.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsSvc.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsTray.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pdfndr.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PerAvir.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qh.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Quick Heal.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QuickHealCleaner.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SafetyKeeper.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Save.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveArmor.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveDefense.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveKeep.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secure Veteran.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\secureveteran.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Security Center.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SecurityFighter.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\securitysoldier.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smart.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smartprotector.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smrtdefp.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SoftSafeness.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spywarexpguard.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrustWarrior.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsc.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\W3asbas.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winav.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windll32.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windows Police Pro.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xpdeluxe.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~1.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~2.exe\ (Trojan.FakeAV) -> Deleted HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Anti-Virus Professional.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntispywarXP2009.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntiVirus_Pro.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPlus\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusPro_2010.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AntivirusXP\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirusxppro2009.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\av360.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brastk.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csc.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\dop.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\frmwrk32.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gav.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbn976rl.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\homeav2010.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MalwareRemoval.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ozn695m5.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pav.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pc.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PC_Antispyware2010.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsAuxs.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsGui.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsSvc.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsTray.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pdfndr.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PerAvir.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\personalguard\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qh.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Quick Heal.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QuickHealCleaner.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rwg\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SafetyKeeper.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Save.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveArmor.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveDefense.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SaveKeep.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Secure Veteran.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\secureveteran.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Security Center.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SecurityFighter.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\securitysoldier.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smart.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smartprotector.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smrtdefp.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SoftSafeness.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spywarexpguard.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrustWarrior.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tsc.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\W3asbas.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\winav.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windll32.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\windows Police Pro.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xp_antispyware.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\xpdeluxe.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~1.exe\ (Trojan.FakeAV) -> PendingDelete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\~2.exe\ (Trojan.FakeAV) -> PendingDelete Potential Unwanted Programs _________________________________________________ HKLM\SOFTWARE\Classes\s\ (Softonic) -> Deleted
-
-
Hallo juisterr (kape),
Dank voor het heropenen van het discussie item.
Heb via hitman pro x64 m'n computer voorlopig kunnen opschonen en een logfile aanmaken. Heb dit op m'n bureaublad geplaatst van m'n gëinfecteerde computer. Nu wens ik dit filetje op te halen via veilige modus, maar deze is niet (meer) bereikbaar.
Na het indrukken van de F11 toets kan ik niet meer weerkeren in veilige modus maar bekom ik een "Cyber Link Power Recover" scherm; waar ik de keuze heb tussen SHUTDOWN REBOOT of NEXT, waar ik vervolgens de keuze heb tussen de selectie van restauration mode: no backup of with backup.
Ter info computer: Medion Windows7
Reboot lijkt me niet aangewezen..;Weet PC helpforum raad met dit nieuwe obstakel?
-
Kan voorlopig nog niet verder.
Aanmaak USB kickstart voor 64bit gëinfecteerde computer dient te gebeuren op eenzelfde 64bit computer, terwijl niet gëinfecteerde computer 32 bits besturingssysteem heeft.
Dus nog even op zoek naar andere computer om gepaste kickstart te maken.
-
Na enkele minuten scriptfout opgetreden:
Regel: 68
Teken:6
Fout: kan het pad niet vinden.
URL:file///C/Windows/System 32/config/SYSTEM~1/AppData/Local/Temp/zoekrun.hta
Na beantwoorden van vraag "wilt u doorgaan met het uitvoeren van script op deze pagina" met ja , blijft script eindeloos runnen
zonder enige log melding.
computer na uurtje bollen dan mijn afgezet.
-
Beste juisterr,
Toch nog maar even wachten aub met reaktie , script is ondertussen aan het lopen
-
Heb programma gedownload via andere computer (windows vista) en nadien uitgepakt op geïnfecteerde computer (windows 7), maar het programma zoek.exe wil niet opstarten na commando "uitvoeren als administrator"
Krijg geen(fout)melding; alles blijft zonder gevolg.
-
Hallo juister,
Heb programmatje geopend na plaatsing op bureaublad ( in veilige modus), maar krijg volgende melding:
Autolt error
Line 7154 (file c\Windows\System32\config\systemprofile\Desktop\RSITx64.exe) Subscript used with non-Array variable
Blijkbaar is het niet mogelijk op deze manier. Heb geen idee wat deze foutmelding betekend?
Zijn er eventueel nog andere mogelijkheden?
-
Beste juisterr,
Ja dit lukt me wel. Kan ik nu RSIT tool instructies zoals hierboven uitvoeren zonder problemen?
leekie
-
Beste juisterr,
Dank voor uw reactie.
Ik heb een Windows 64bit versie op m'n computer.
Wat ik echter niet begrijp is hoe ik deze tools kan uitvoeren, als ik niet kan inloggen of aan m'n bureaublad raak?
Dien ik bepaalde handelingen (vooraf) uit te voeren via veilige modus? Hoe ga ik hier te werk?
met dank,
leekie
-
Beste PC Helpforum,
Onlangs werd m'n computer door malware vergrendeld tijdens het opstarten. Wegens tijdsgebrek had ik toen de werksessie niet voortgezet.
Nu vandaag bij het opstarten verloopt alles normaal tot bij het windows7 scherm waar ik na het invoeren van m'n passwoord de mededeling krijg" De service User Profile Service verhinderd het aanmelden . Gebruikersprofiel kan niet worden geladen"
Kan iemand me tips geven om me verlossen van deze kwelgeest?
Met dank,
Leekie
-
-
Wegens slechte koeling is een onderdeel op het moederbord van mijn computer gedeeltelijk verbrand, hierdoor valt mijn computer regelmatig uit tijdens het werken.(moederbord INTEL D865GBF/D865GLC )Kan dit moederbord of het bewuste onderdeel (zie foto) nog worden bekomen? Kent iemand het typenummer van het bewuste onderdeel?
Met dank,





Heropend
in Archief Bestrijding malware & virussen
Geplaatst:
Even opgezocht.
Heb de MEDION Recovery disc (windows 7 Home premium SP1), alsook de application & support disc